Banyan Security Test Drive - Explore the Banyan Security Command Center
Overview
Banyan Security’s SaaS-based Cloud Command Center centralizes the management of your organization’s entire Zero Trust infrastructure, such as:
- Organize an inventory of your Users and Devices
- Define a catalog of service tunnels, hosted websites, infrastructure services (SSH, TCP, RDP, and Kubernetes), and SaaS apps
- Specify roles and policies to manage access controls
- Tailor TrustScore settings and in-app remediation instructions for end users
- Customize deployment options and registration methods
- Configure settings to integrate with third-party identity providers
This scenario will illustrate the day-to-day experience of a Banyan administrator within the Command Center.
Contents:
Before You Begin
For this Test Drive scenario, you will need:
- A valid set of credentials to MedSoft’s Identity Provider (Okta)
Explore the Command Center
Review Reports and Events
1. Launch your preferred browser and navigate to the Banyan Command Center. Enter the organization name test-drive and then click SUBMIT.
Enter org name as `test-drive`
2. Click Continue to login via our SAML Identity Provider, Okta.

Click Continue to log
3. Enter credentials you have been provided to sign in via Okta:
Enter your provided credentials
4. Navigate to Monitor > Reporting and then explore high-level visualizations of data related to this organization, including:
- Access activity - Total counts and breakdowns of your devices, users, services, policies, roles, and Access Tiers.
- Access patterns - Most popular services by user, most active users by service, and more.
- TrustScore intelligence - Path of Zero Trust access from device (operating system) through Trust Level to service.
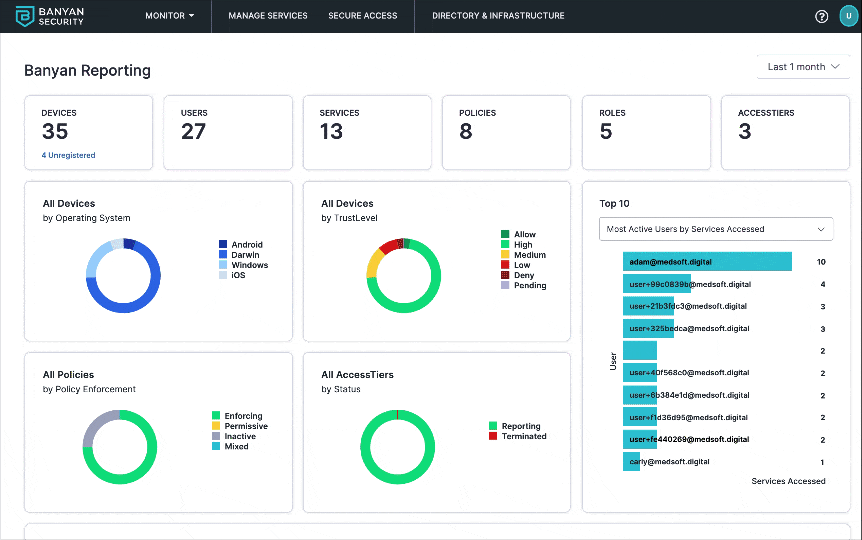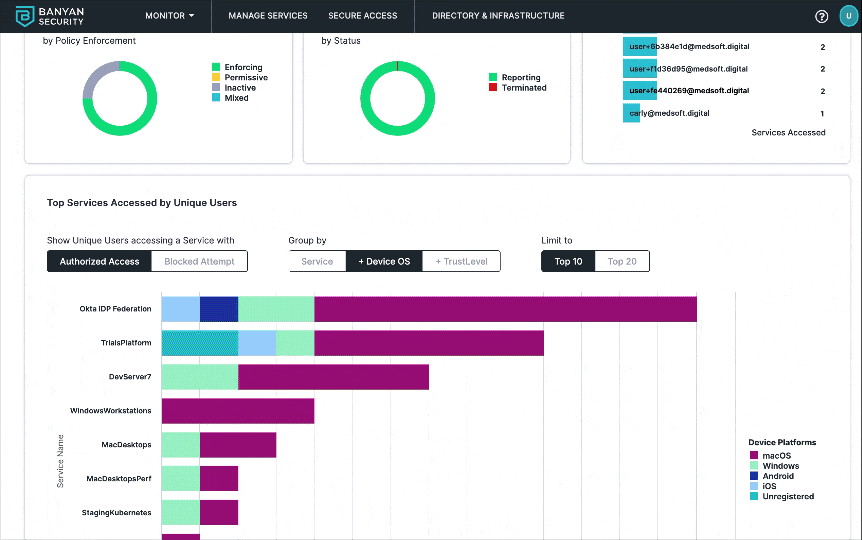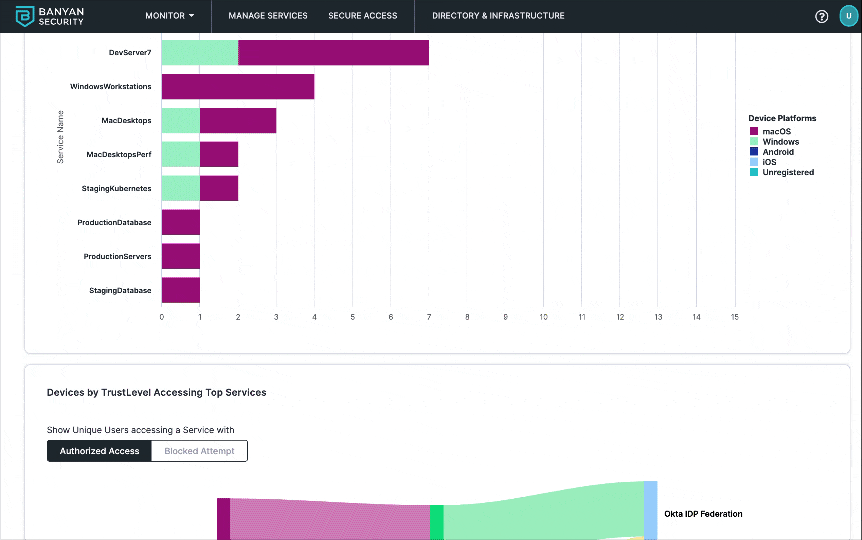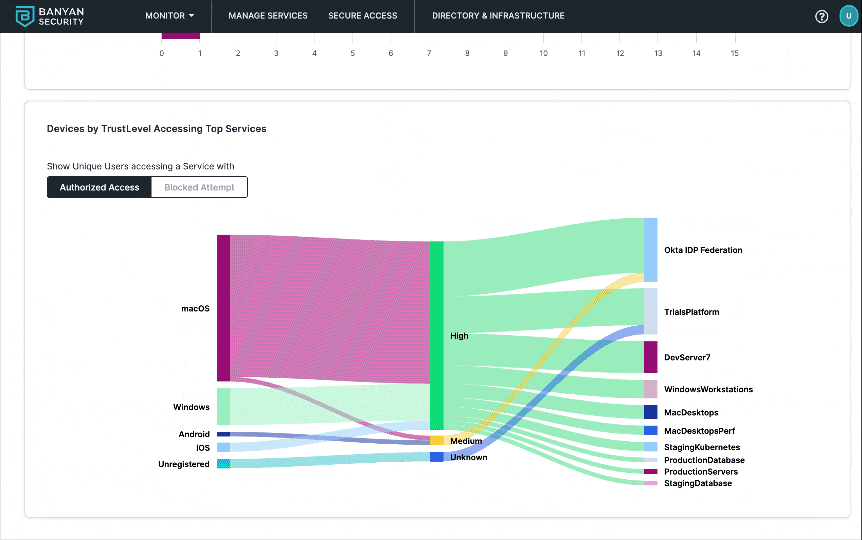
Banyan Reporting page
5. Scroll down the page to find the Devices by TrustLevel Accessing Top Services graph and review a breakdown of unique users making authorized and blocked access attempts to individual services. This details the Zero Trust journey as we provide trust-based access control across protected endpoints and services. You get full visibility into the TrustScores of devices accessing the protected services.
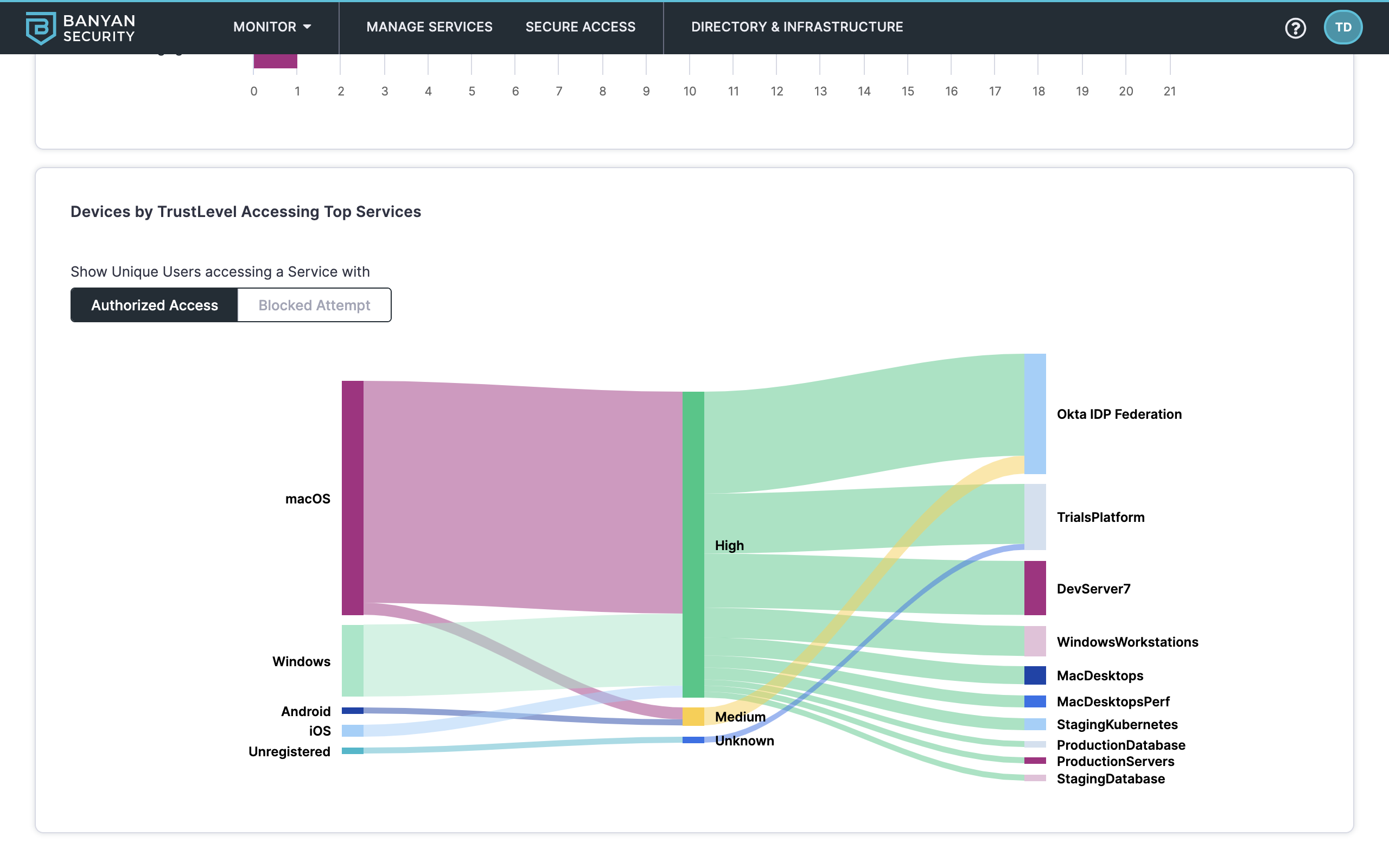
Devices by TrustLevel Accessing Top Services diagram
6. Navigate to Monitor > Events to filter and explore lists of events from the organization’s system log.
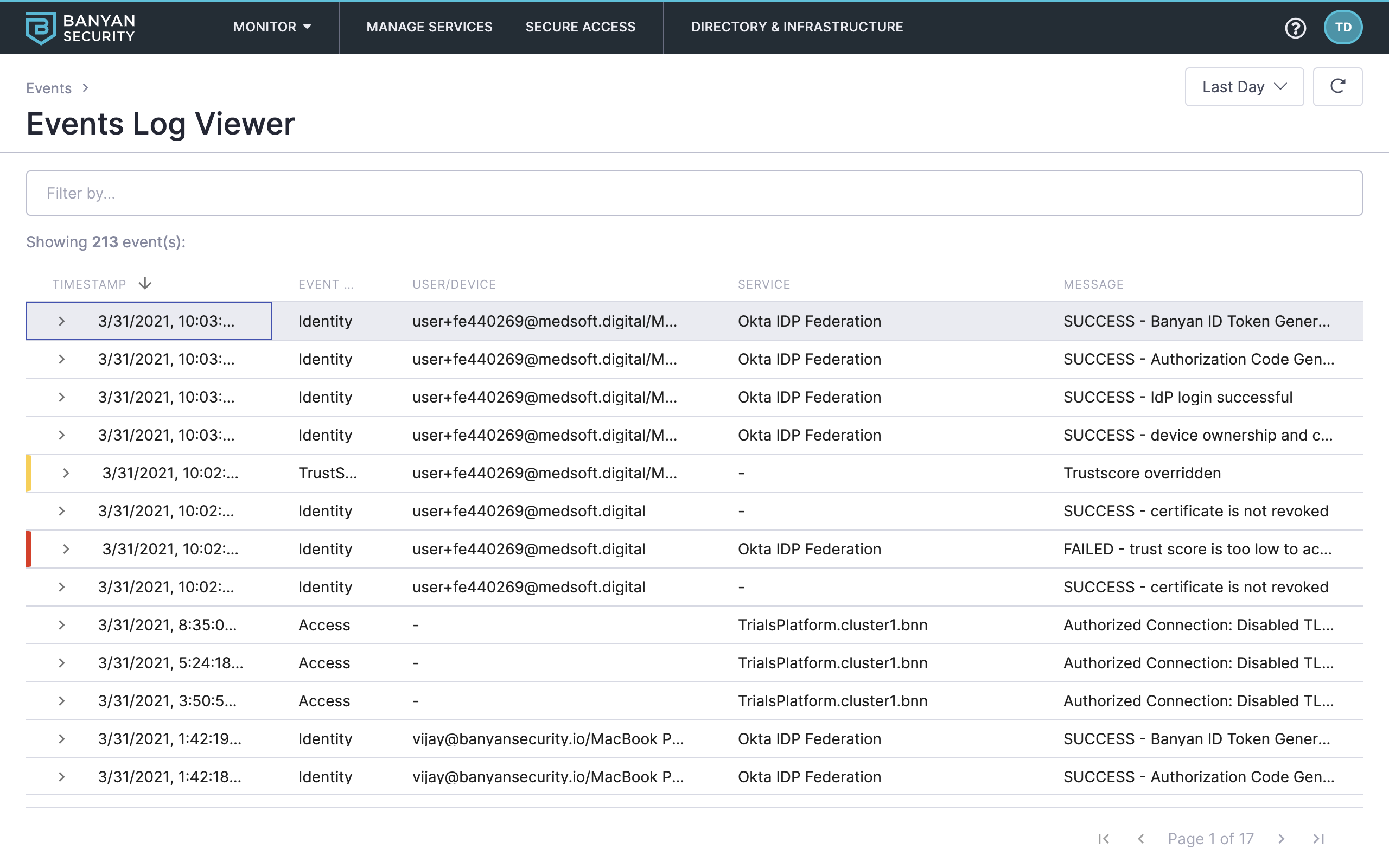
Events Log Viewer
7. Use the date picker and filters to explore Banyan events. For example, set the date range to Last Week and then filter events in the following order:
- Event Type: Access
- Event Severity: ERROR
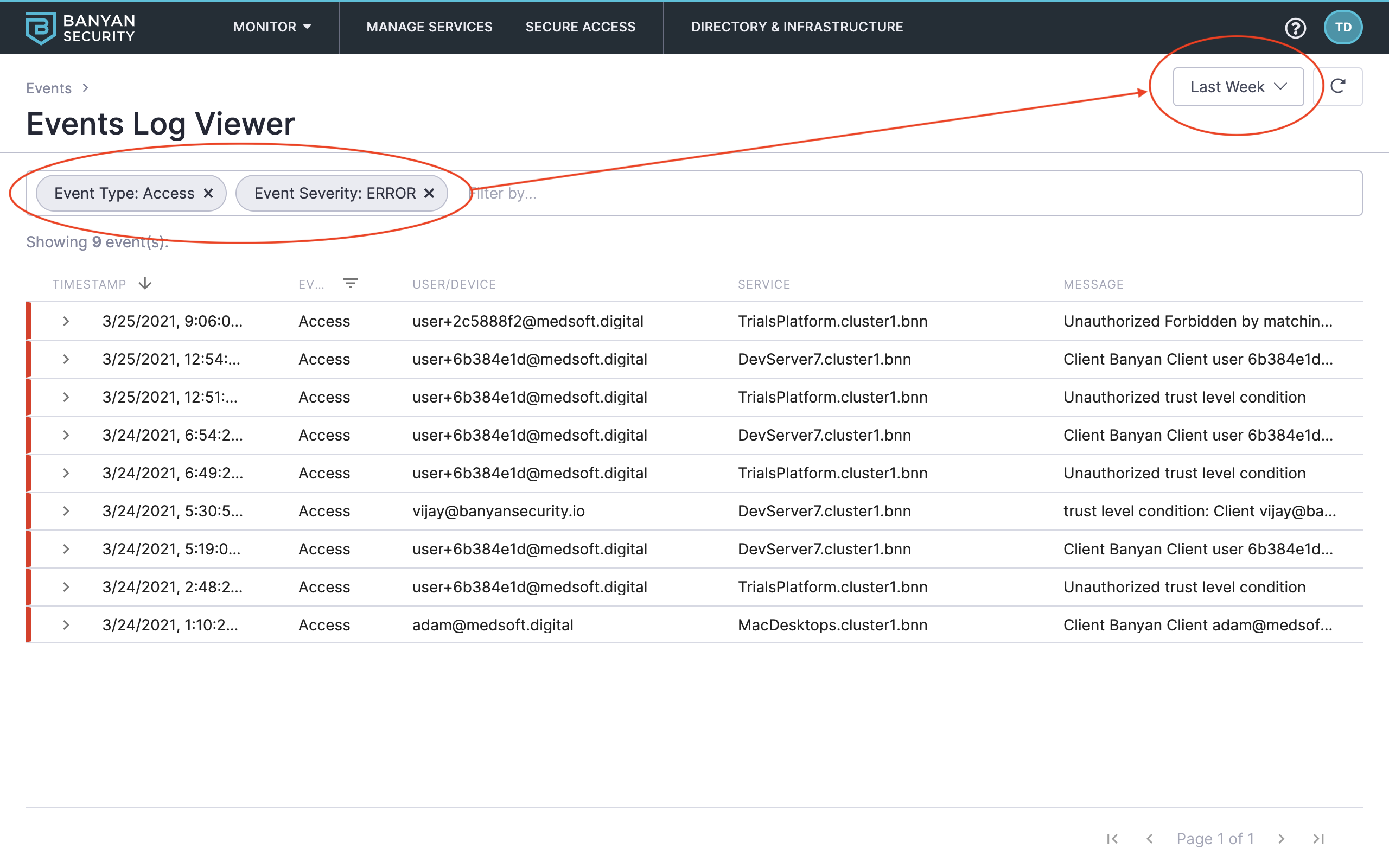
Review denied access attempts in the last week
This shows denied errors and specific reasons why access was denied. As you move through the other Test Drive scenarios, you’ll see other events populate here as well.
Read more about reporting and events in our product docs:
Audit Directory (Users and Devices) and Infrastructure
Now that we’ve covered reports and events, let’s see which users, devices, and infrastructure components are associated with our organization.
Banyan integrates directly with your Identity Provider (Okta, Azure AD, G Suite, OneLogin) and MDM tools (Workspace ONE UEM, Jamf Pro, Intune) to create and manage a directory of users that can access your Services.
8. Navigate to Directory & Infrastructure > Directory > Users.
Navigate to Directory & Infrastructure
9. Click into a user record (such as Adam Admin) to review its specifications, user access activity, roles, and more.
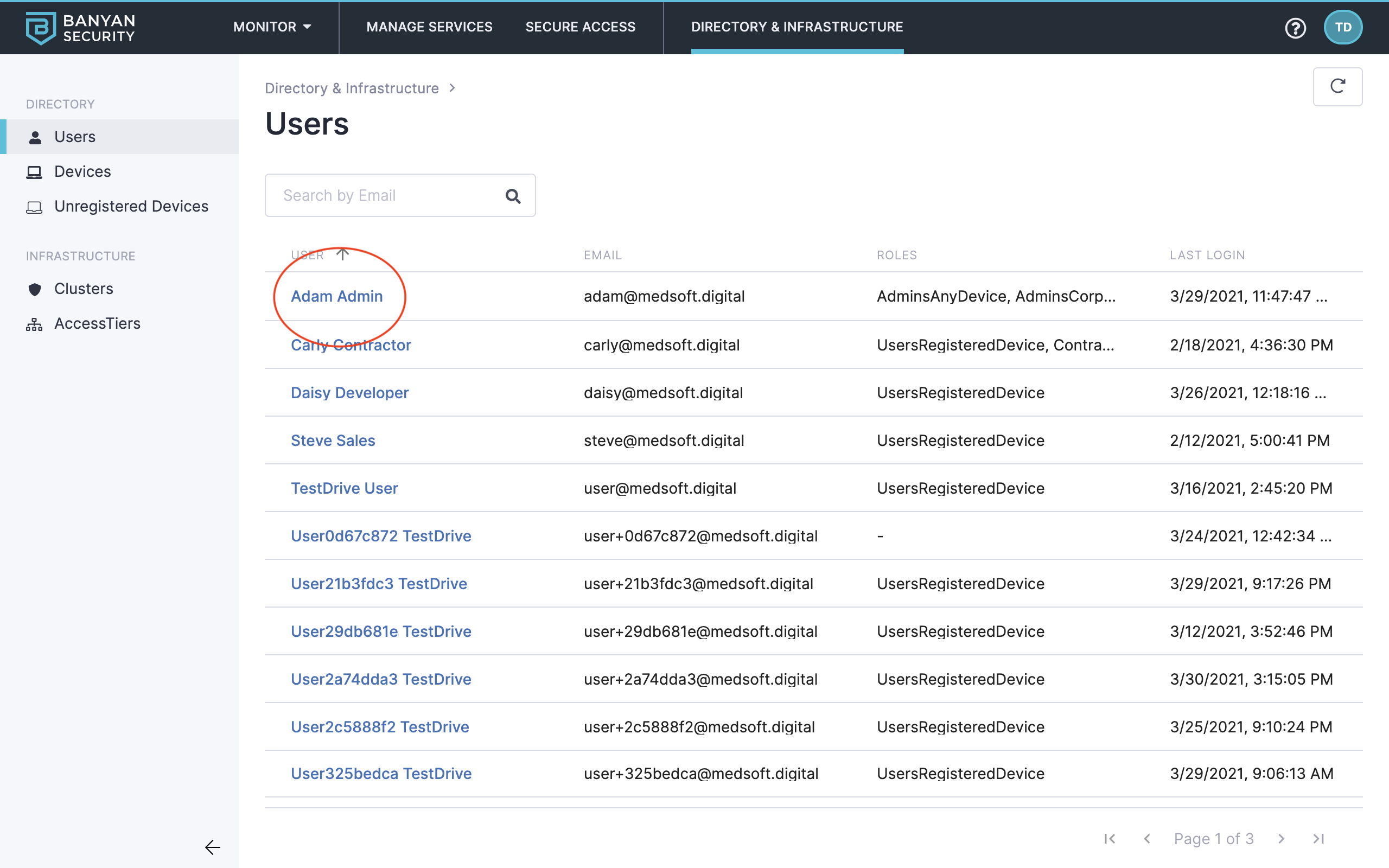
Users overview
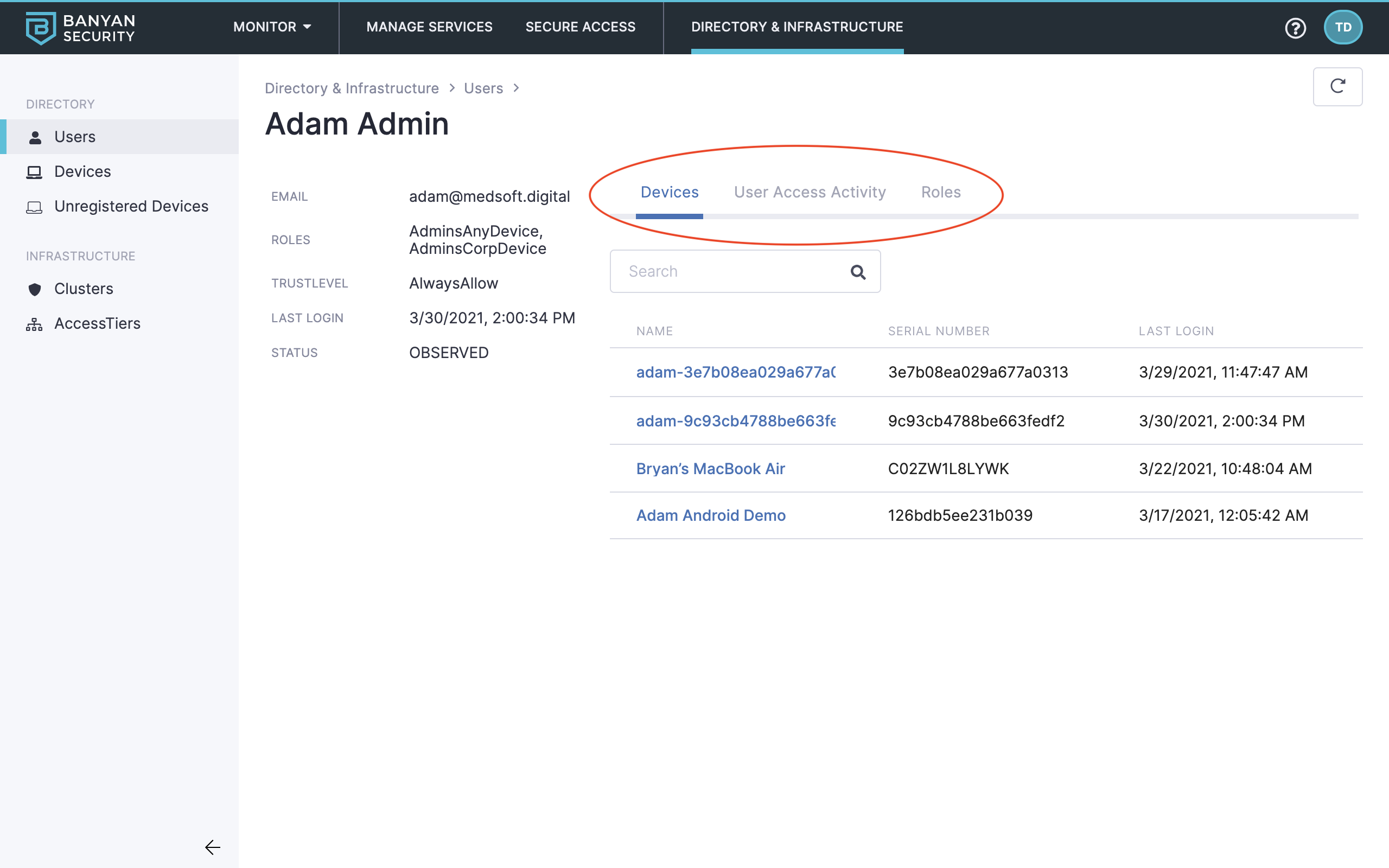
User details
10. On the left navigation menu, explore the Devices and Unregistered Devices tabs. (The Test Drive organization allows Unregistered Devices to access Banyan-protected services.)
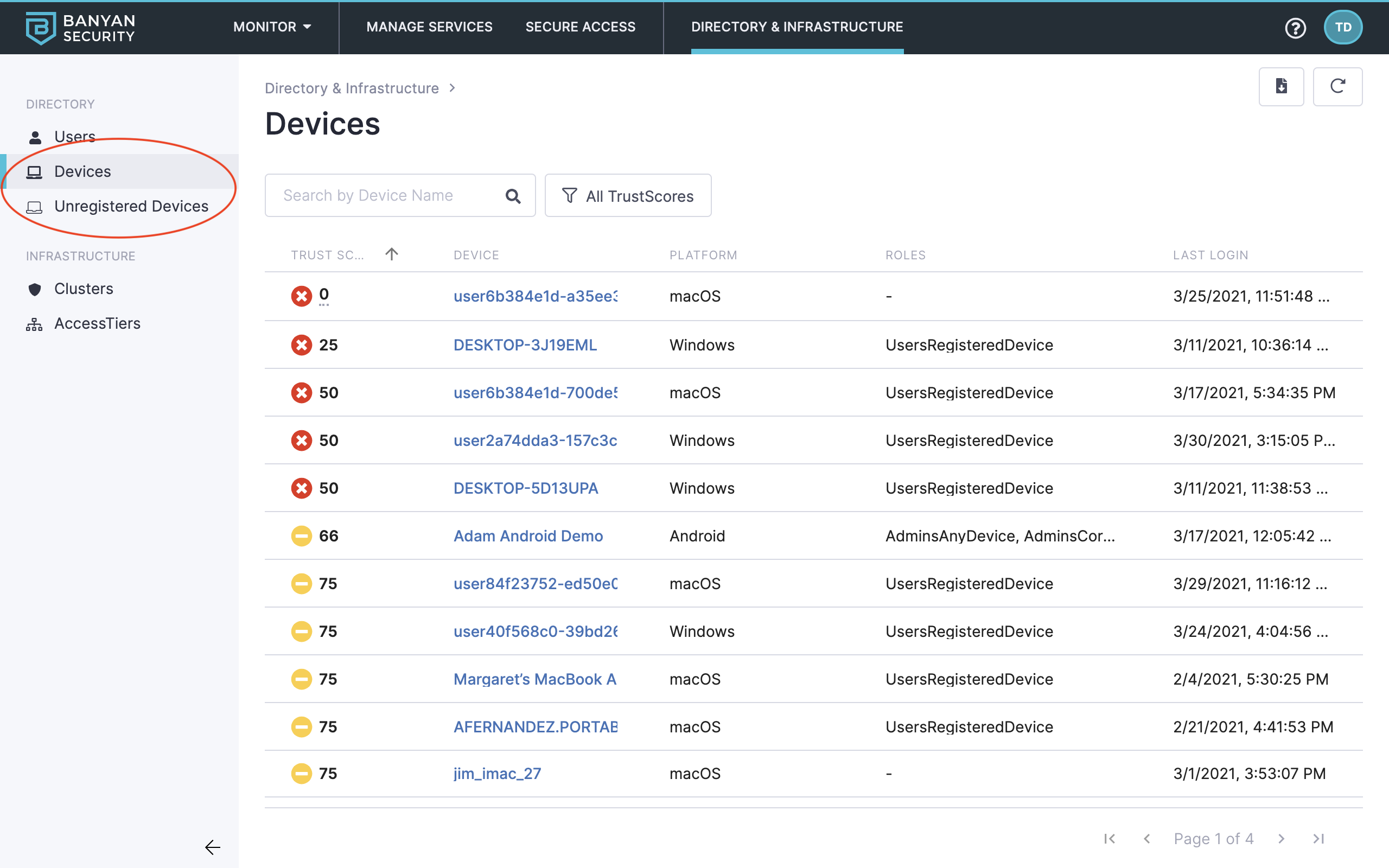
Devices and unregistered devices
You can see devices and TrustScores here. For devices having low TrustScores, you can reach out to end users to make their devices more secure, and ask them follow in-app self-remediation instructions.
11. Also on the left navigation menu, explore the Infrastructure components at play, such as Clusters and Access Tiers.
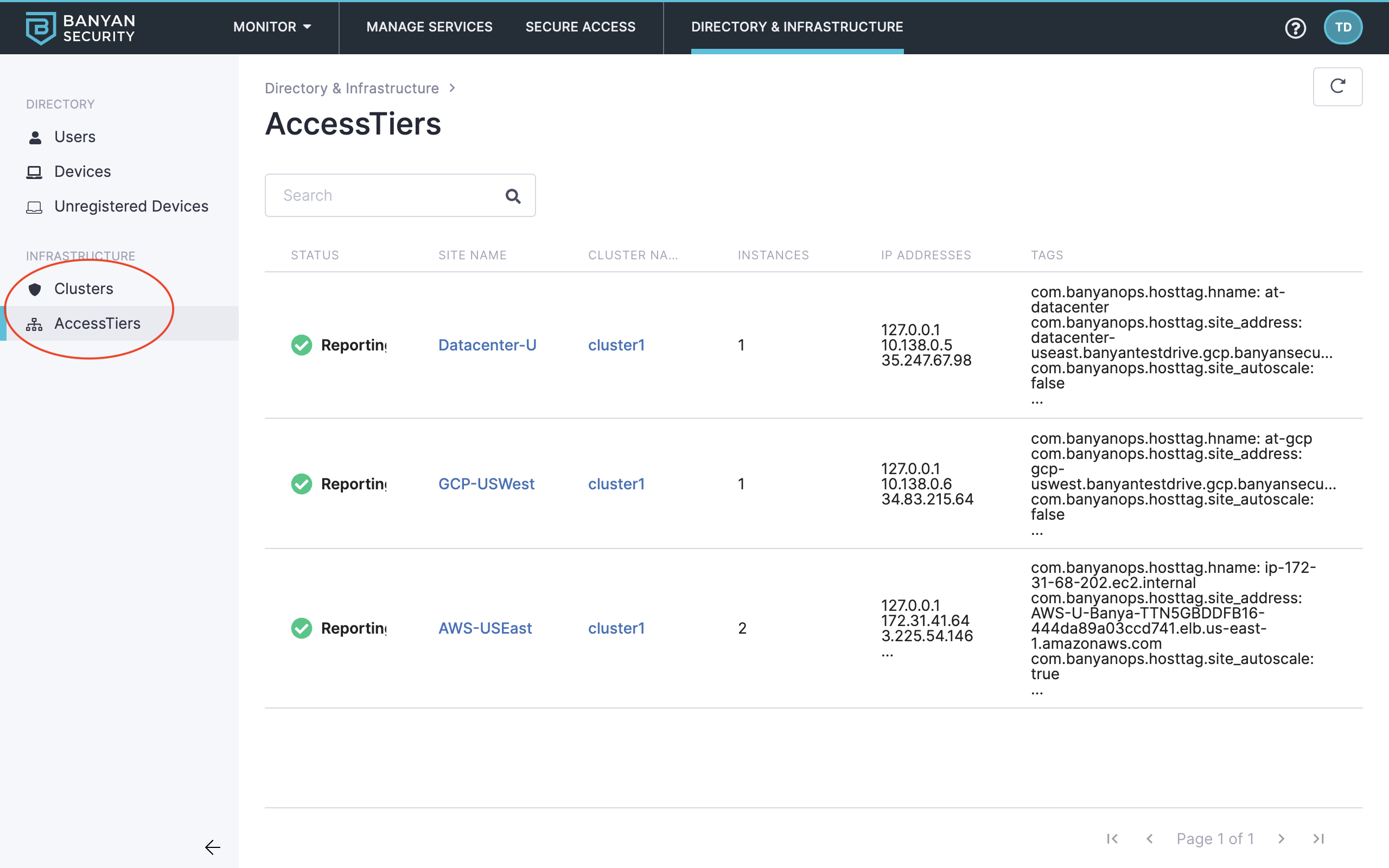
Clusters and Access Tiers
Read more about Directory & Infrastructure in our product docs:
Secure Access via Roles & Policies
Banyan has developed a simple, human-readable policy framework to implement Zero Trust access controls that use the concepts of:
- Role – A set of access privileges, which are defined by specific attributes of entities (such as email, group membership, device ownership, etc).
- Policy – An authorization rule that specifies who can access resources exposed by a service.
The specific access privileges of a Role are determined by the Policies that mention the Role.
To review configured the Roles and Policies directly associated with your Test Drive experience:
12. Navigate to Secure Access > Roles.
Navigate to Roles
13. Select the AdminsAnyDevice role and then review the role’s specifications and associated users and devices.
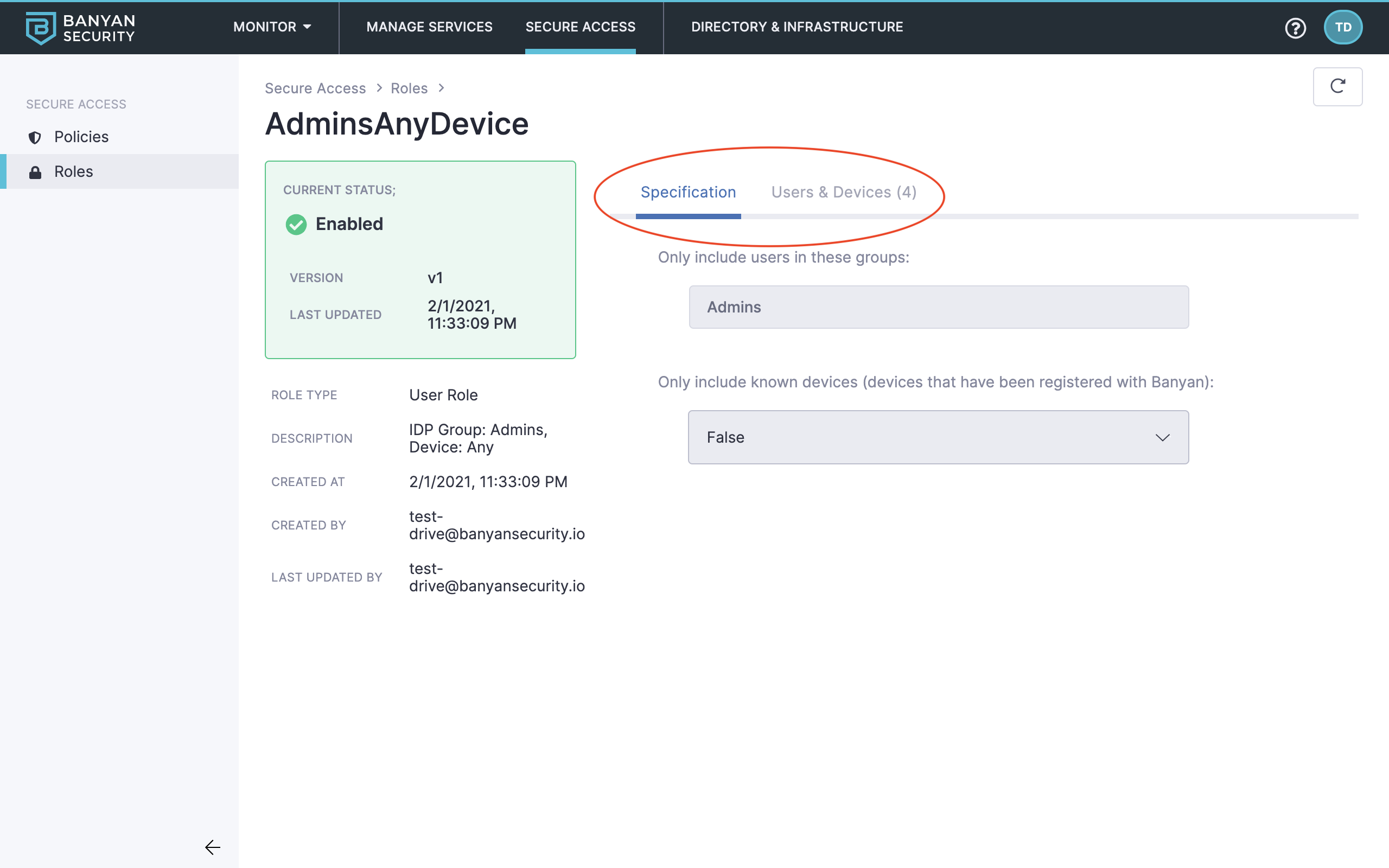
Role details
14. Navigate to Policies.
Navigate to Policies
15. Select the AdminsOnly Infra policy and then review the policy’s specifications and associated services.
Policy details
Read more about Roles & Policies in our product docs:
Manage Services
Now that we know which Roles and Policies allow us to Test Drive this scenario, let’s see which Services have been configured and protected by Banyan.
The Banyan Command Center allows you to use templates to define and secure different types of corporate resources using Zero Trust policies:
- Hosted Services – Includes Hosted Websites and Infrastructure Services (such as SSH, RDP, Kubernetes, and Generic TCP).
- SaaS Applications (Banyan-first) – SaaS applications configured for SAML/OIDC authentication using Banyan TrustProvider.
- IDP Routed (IDP-first) – SaaS applications configured for SAML/OIDC authentication using your Identity Provider to federate to Banyan TrustProvider.
Additionally, you can create Custom Hosted Services for advanced use cases.
16. Navigate to Manage Services > Hosted Services.
Navigate to Manage Services
17. Locate the OktaSSO service, and then click it to review its specifications, access activity, and more.
Select OktaSSO
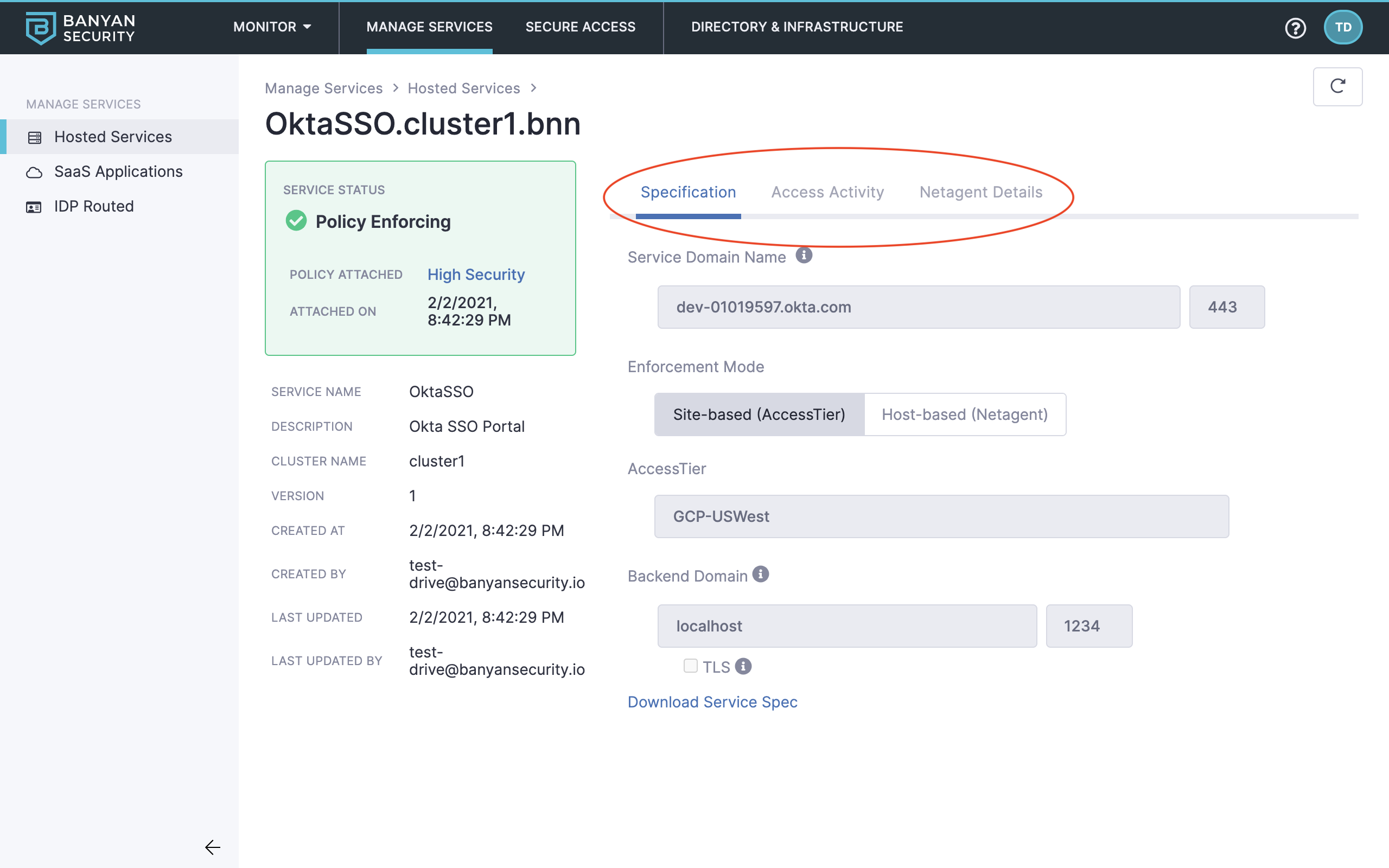
Review service details
Read more about Services in our product docs:
- Use Cases and Flow Diagrams
- Manage Services
- Secure Hosted Websites
- Secure Infrastructure Services
- Secure SaaS Applications
How It Works
Banyan Command Center is a global management console for IT Administrators and Security teams to manage the Banyan solution. You can interact with the Command Center via the web portal or the RESTful API, to develop and enforce policies, configure alerts for security events, and visualize real-time connectivity.
The Banyan Command Center includes two subcomponents:
- Banyan Shield is a Cluster Coordinator, deployed one per logical cluster. Shield manages a Private PKI (Public Key Infrastructure) to distribute X.509 Certificates to clients and services in your organization.
- Banyan TrustProvider is a Federated Authentication Manager that uses OpenID Connect / OAuth-based workflows to authenticate end users and devices. TrustProvider integrates with your Identity Providers and Device Managers to deliver short-lived certificates to authenticated end users on approved devices.
The Management Components are hosted by Banyan as a Software-As-A-Service (SaaS) offering.
Ready to see more? Give another Test Drive scenario a spin!
