Banyan Security Test Drive - Infrastructure Access
Overview
Access to Infrastructure Services, such as SSH/RDP Servers, Kubernetes, General TCP, and Databases, is regularly needed by all Operations and Engineering team members. Traditionally, access relies on VPNs - generating long-lived passwords or, sometimes, long-lived SSH key-pair per user. Long-lived credentials and keys can be a security nightmare, given the ease with which they can be shared or lost.
In this scenario, MedSoft has published various development resources via the Banyan services catalog. We will showcase a single click access flow all the way through to an SSH Server as well as Just-In-Time user creation.
Contents:
- Before You Begin
- One-click SSH Access to Linux Servers
- Access a Server via SSH
- Change Device Posture
- How it Works
- Need Additional Assistance?
Before You Begin
For this Test Drive scenario, you will need:
- A valid set of credentials to MedSoft’s Identity Provider (Okta)
- A MacOS or Windows device registered with the Banyan Desktop App (v2.0 or higher)
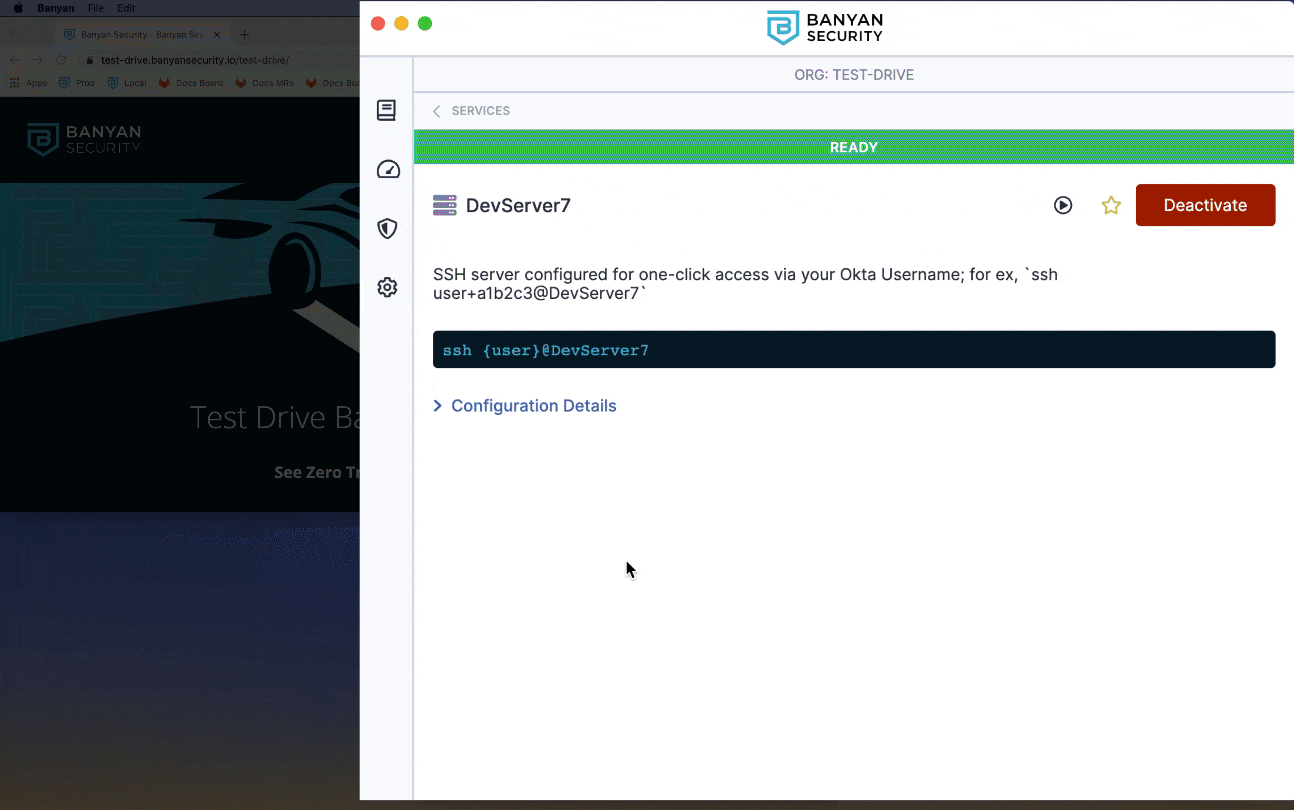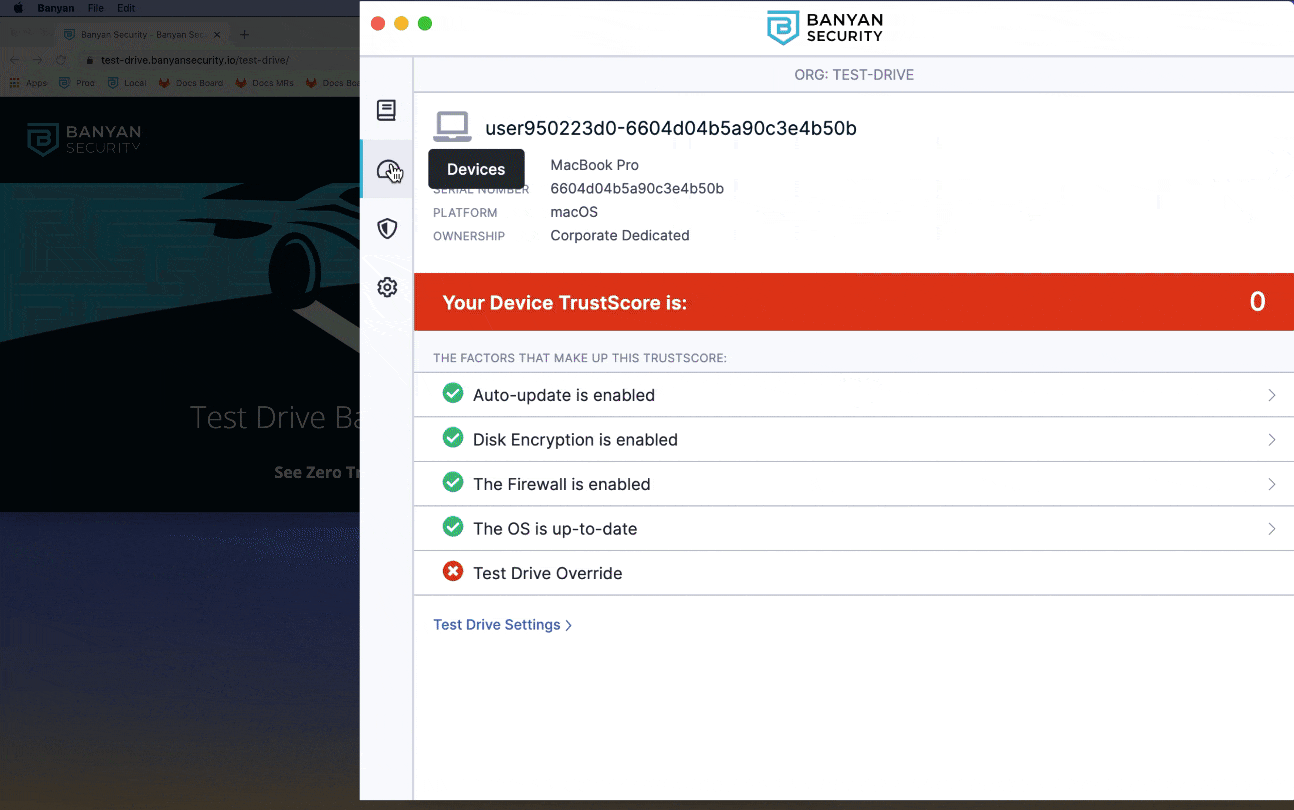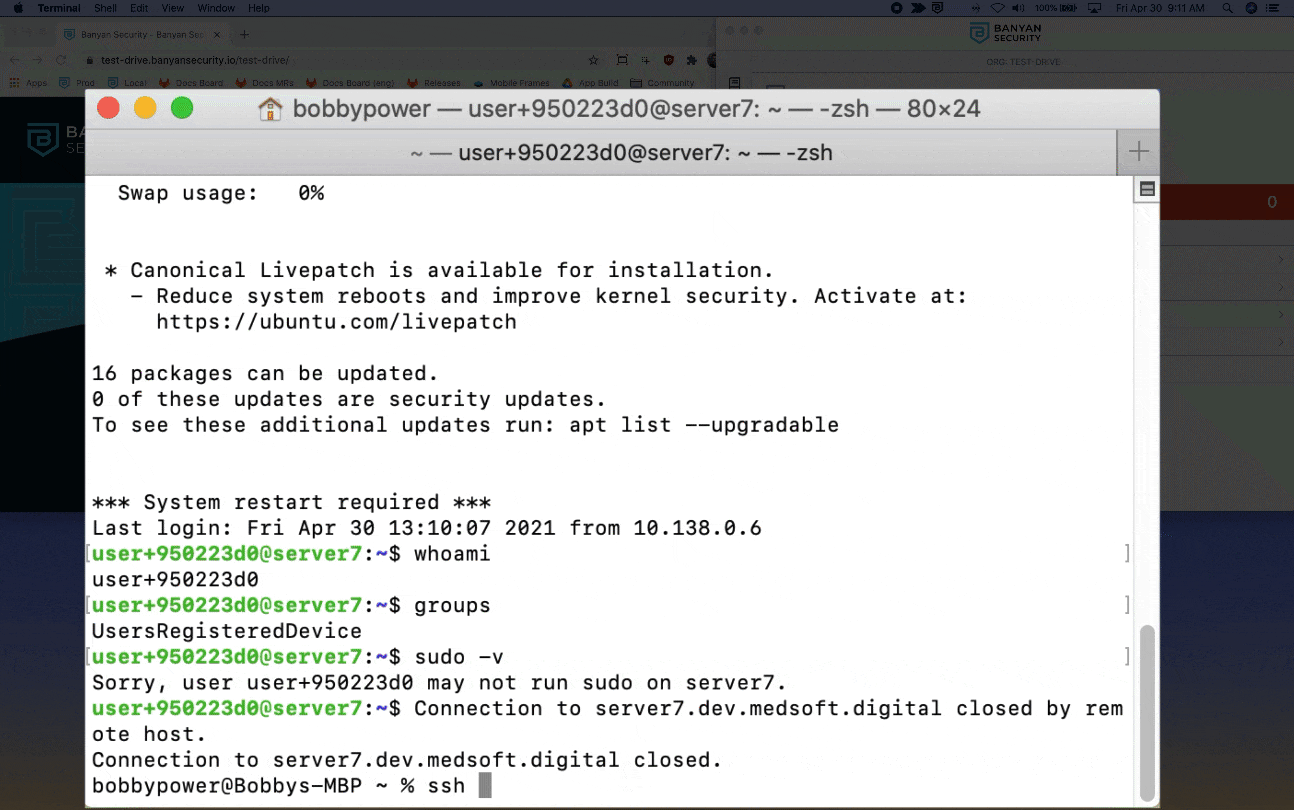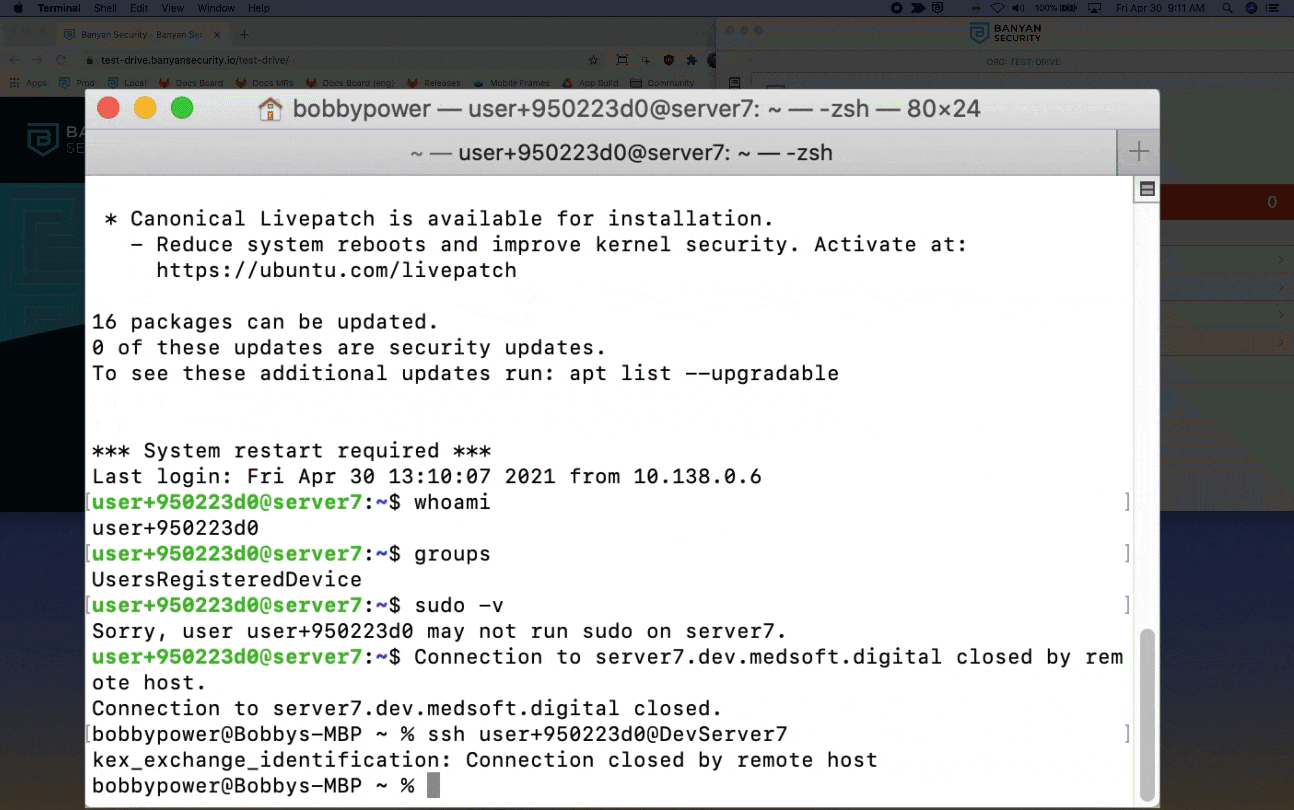
- A minimum device TrustScore of 61 or higher
- If your TrustScore is 60 or lower, review the in-app remediation instructions
- Then, navigate to Settings and click Send Devices Features to update your TrustScore
One-click SSH Access to Linux Servers
Access a Server via SSH
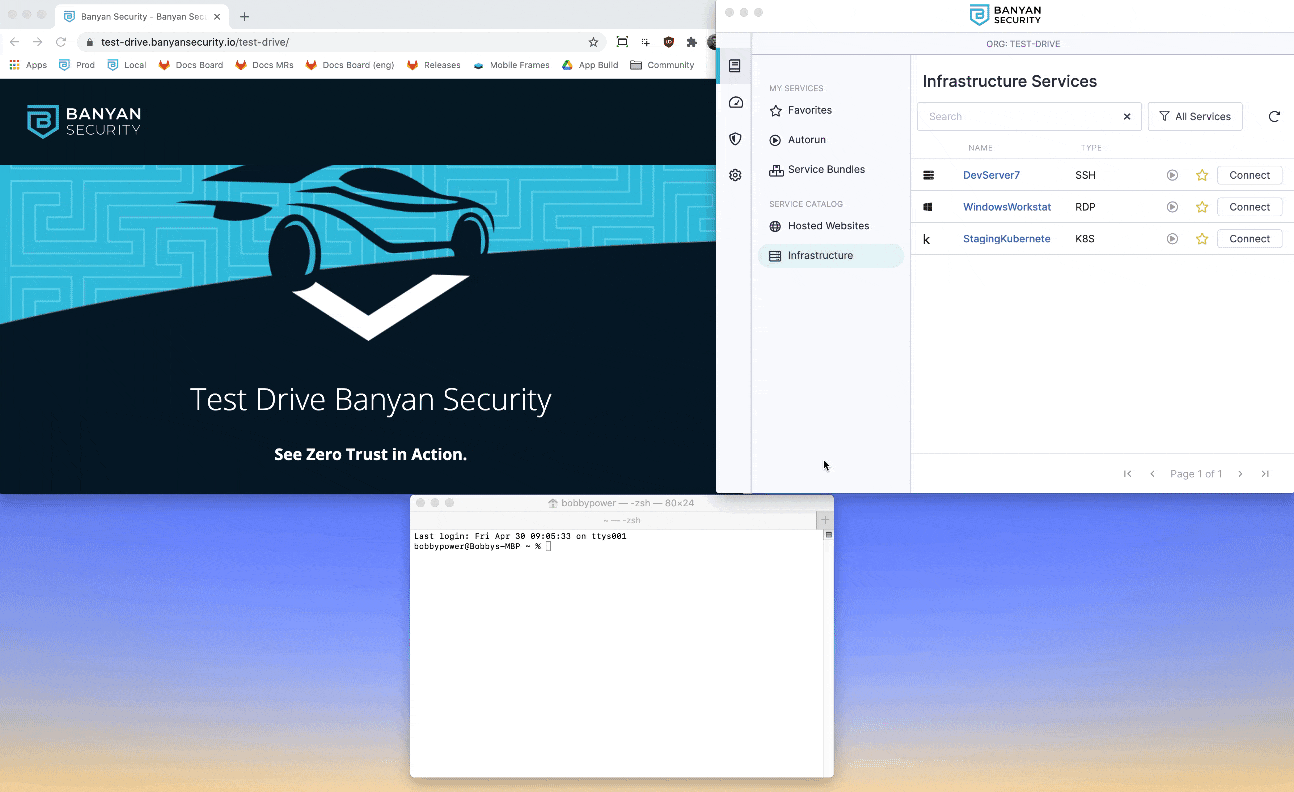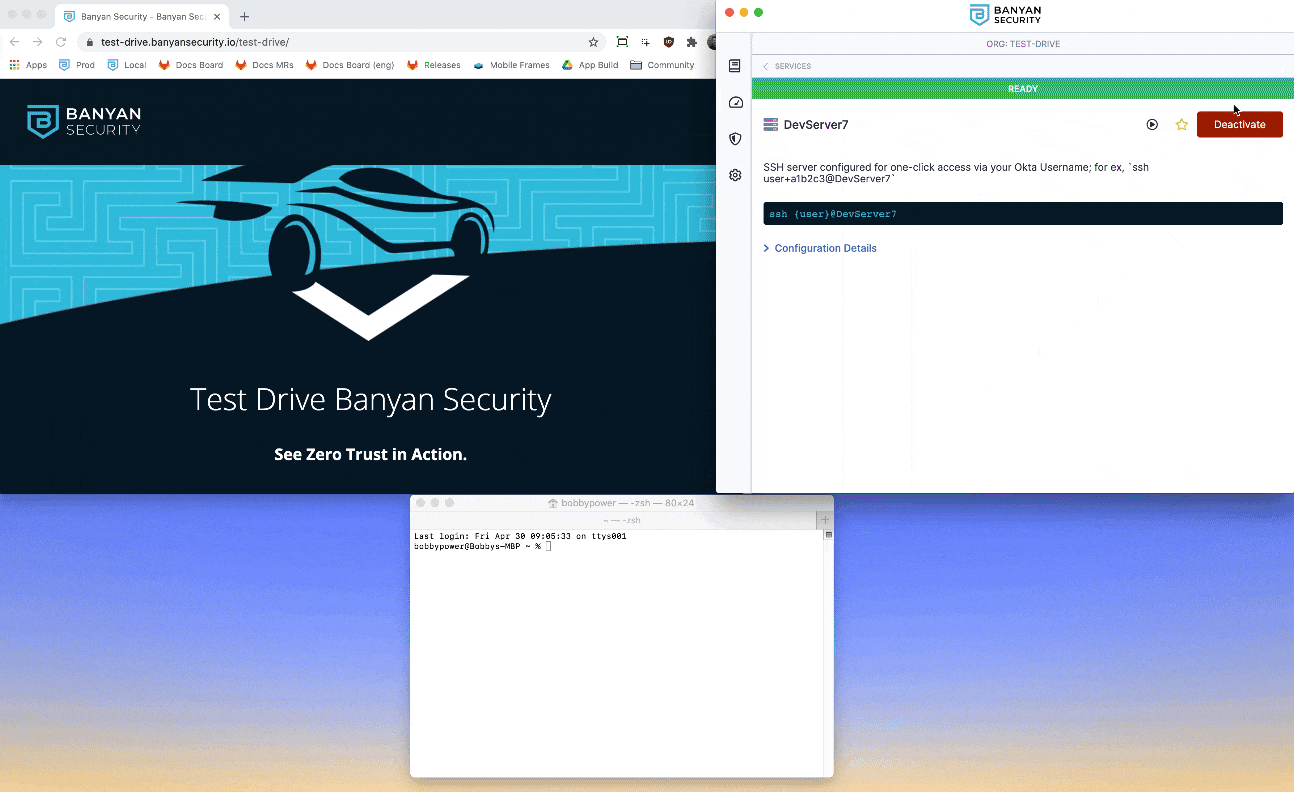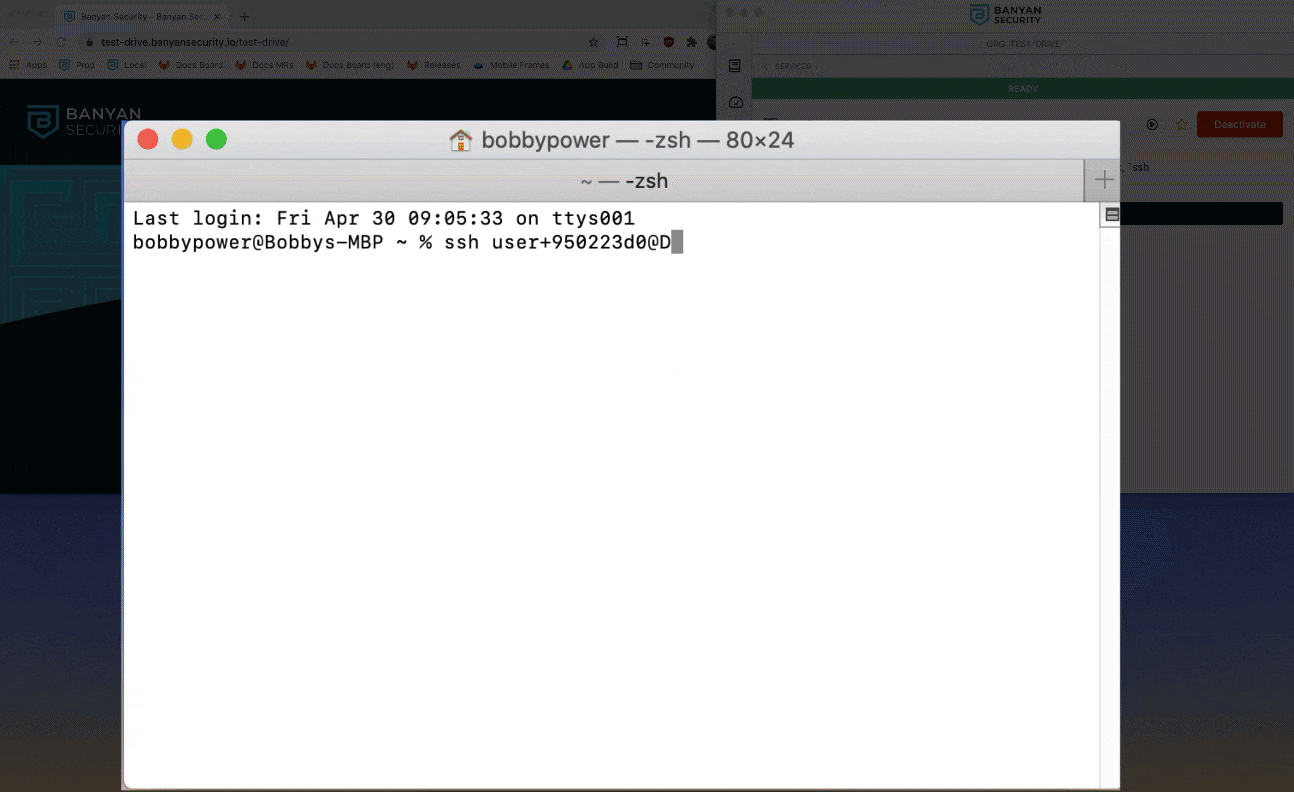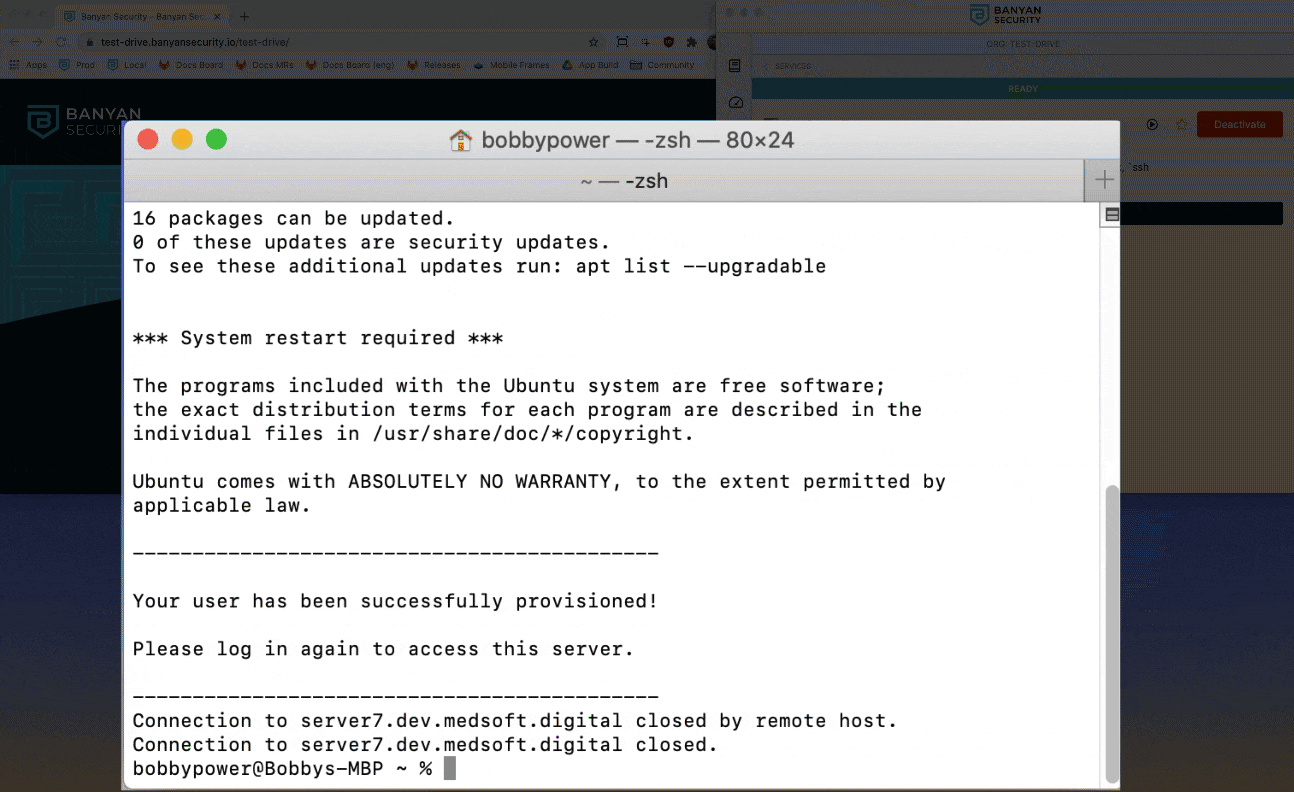
MedSoft publishes various development resources via the Banyan service catalog.
1. Launch the Banyan App from your device Menu Bar (macOS) or Taskbar (Windows), and then click Login to access other services to authenticate and populate infrastructure services, such as SSH and Kubernetes.
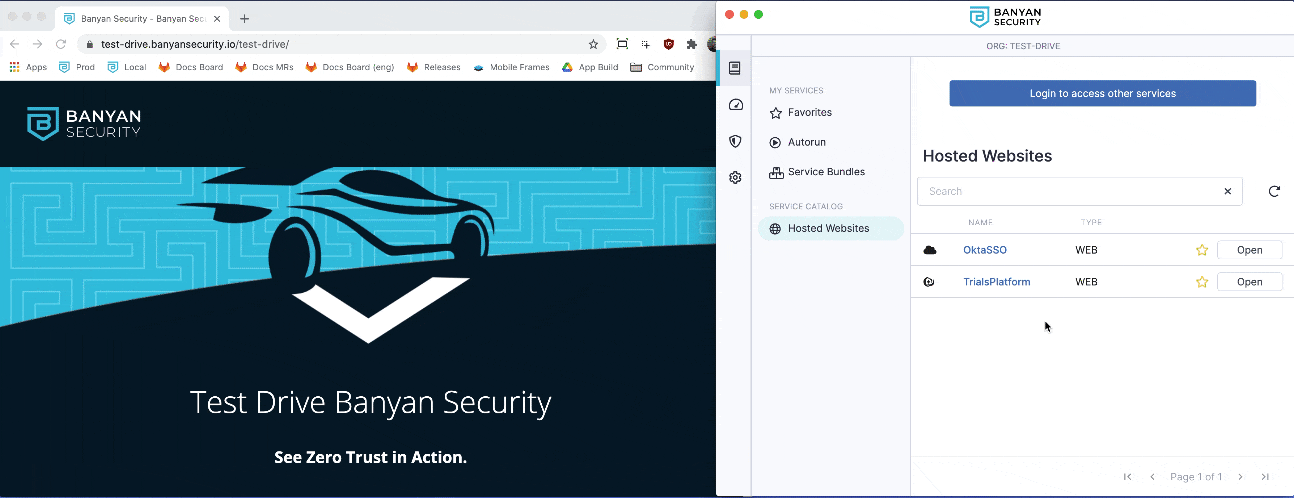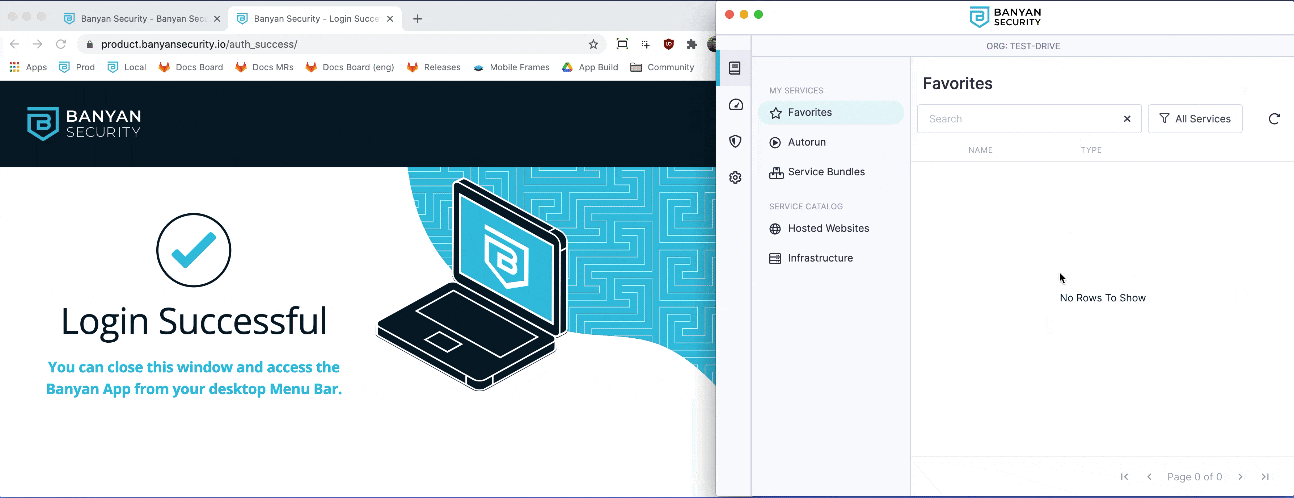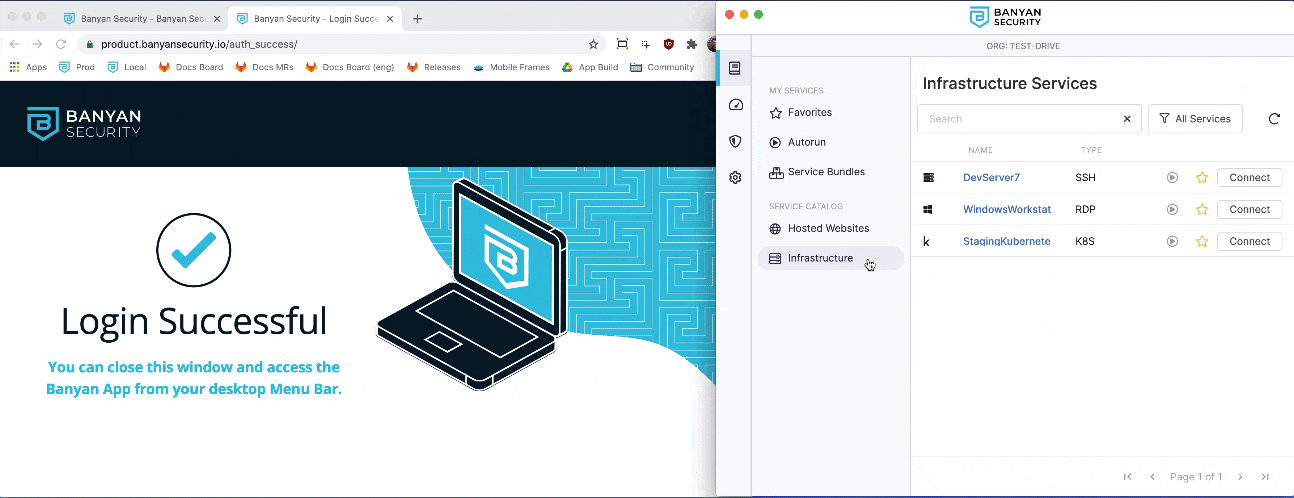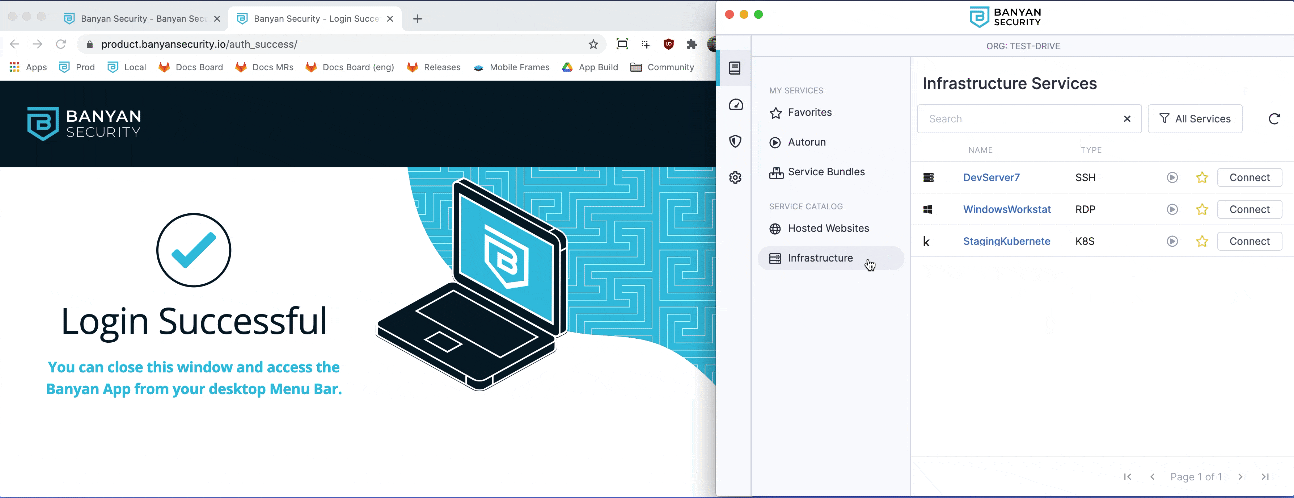
2. Locate the DevServer7 SSH service, and then click Connect. Then, click Activate to start the Banyan Proxy.
3. Launch your OpenSSH client (such as Terminal for macOS or equivalent Command Line tool for Windows) and run the command displayed in the Banyan App, using your Okta username (which is of the form user+123456, without @medsoft.digital).
ssh <YOUR_OKTA_USERNAME>@DevServer7
Keep in mind: We have enabled Just-In-Time user creation, so a new Linux user account and home directory are provisioned for you the first time you access the server. Since this is your first time accessing the server, you are prompted to accept this user creation and group assignment. You will not see this prompt again.
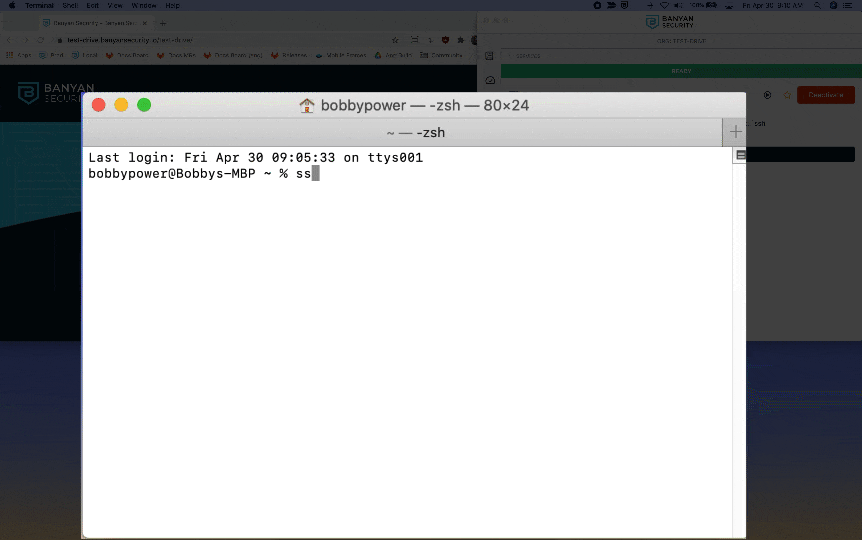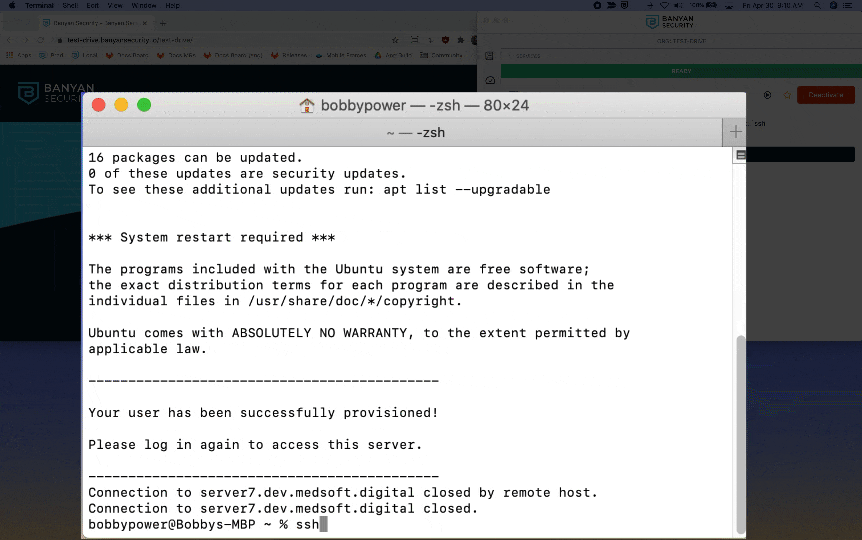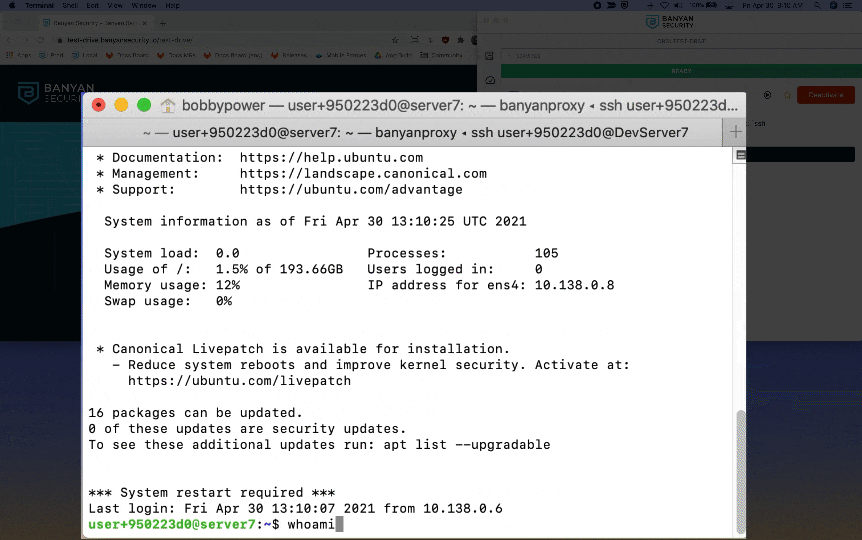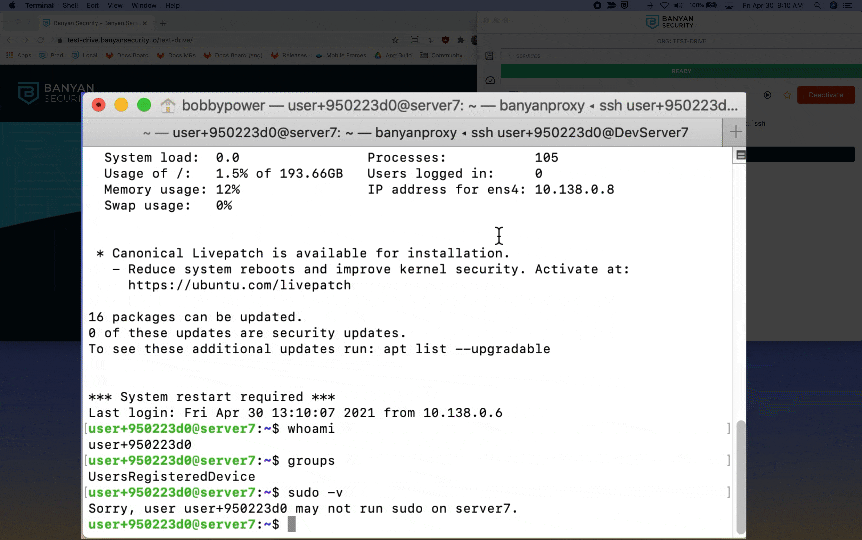
4. Then, run the command ssh <YOUR_OKTA_USERNAME>@DevServer7 again. SSH RBAC is automatically applied, so you have limited access to the server but cannot assume root privileges or run certain commands.
Change Device Posture
Now, let’s see how Banyan Security enforces Zero Trust policies in real-time.
5. To compromise your device posture, click Test Drive Settings and then toggle Lower My TrustScore to the right. Your TrustScore drops to 0, and as a result you can no longer access the SSH server.
This is clearly a simulated scenario. In real life, an end user’s TrustScore drops generally because their device was not patched, their antivirus tool detected some malware, or other vulnerability was detected.
How It Works
Banyan adds on a modern mandatory access control layer that constantly evaluates the security posture of the device and integrates with your organization’s Single Sign On provider. All traffic to infrastructure services is transparently upgraded to Mutual-Auth TLS using short-lived X509 certificates. Security policies can then be continuously enforced, locking down access to specific servers based on user and device attributes and trust levels.
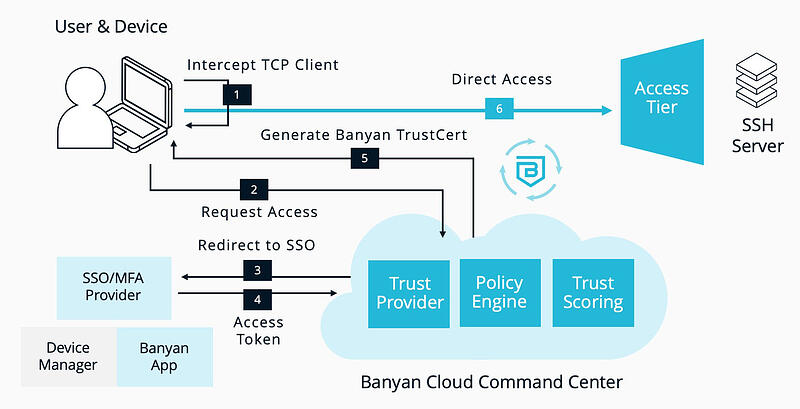
Read more about protecting Infrastructure Services in our product docs:
- Infrastructure Services
- Advanced SSH capabilities including audit logging
- One-click access to K8s clusters
Need a bit of assistance?
Watch the video demo of this Test Drive scenario below.
Ready to see more? Give another Test Drive scenario a spin!
